Difference between revisions of "E-Government Case Study"
(gnAJnEazKxaWYOaMVt) |
m (Protected "E-Government Case Study": Excessive vandalism ([edit=autoconfirmed] (indefinite) [move=autoconfirmed] (indefinite))) |
||
| (96 intermediate revisions by 64 users not shown) | |||
| Line 1: | Line 1: | ||
| − | + | ==Description== | |
| − | + | ||
| + | Usually when a citizen needs some document from the public sector, he has to go to the appropriate | ||
| + | department; often the time spent in queues, and the time spent to reach the right office is very long. | ||
| + | E-Government is the process to make information technologies available to the government services in | ||
| + | order to improve the relationships between citizens and their governments (public sector could be made | ||
| + | open and transparent to the citizens). One of the services made available to the user, is the possibility to | ||
| + | submit applications to require some service, and receive replies online. At any time during the day, from | ||
| + | their locations citizens can access to the offered services and obtain all the needed information without | ||
| + | spending any time in queues. In such a way, e-government is able to improve the efficiency of public | ||
| + | sector, avoiding the time spent to reach different offices or waiting in queue, resulting in an improvement | ||
| + | of the offered services and a better accessibility and transparency of the public services. Not only citizens | ||
| + | may be the the users of the government application, but we can image that all the government agencies | ||
| + | of a city could share data about the citizens and have the need to access to the services of the application, | ||
| + | in order to make available, at any time, all the needed information. The case study is derived from the | ||
| + | EU project NEXOF. In particular, it has been proposed by Engineering Ingegneria Informatica and TIS. We have mapped it into the format proposed for S-Cube, retrieving the business goals and the scenarios needed for our description. | ||
| + | |||
| + | ==Business Goals and Domain Assumptions== | ||
| + | |||
| + | In the following sections will be reported the Business Goals and the Domain Assumptions for the current | ||
| + | case study. | ||
| + | |||
| + | === Business Goals === | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG1. Business Goal TIS-BG-1 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-1 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Statewide provision of online services for citizens, companies, government agencies | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | The infrastructure must be able to make services of the public sector available to all the users, such as citizens, companies or government agencies. Each user can access, from somewhere, to the services providing login information; after the login the user can have the possibility to forward requests of some documents or require any service. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | Essentially the rationale is the capability to make available the services offered by the public sector to citizens, companies and government agencies. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | Users and Public Body | ||
| + | |||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG2. Business Goal TIS-BG-2 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-2 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Improve speed and efficacy of processes | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | The infrastructure must be able to serve quickly the user requests. When a citizen requires a service, replies are received online. Moreover if a fee must be paid, user could access, easily, the e-payment service. At the end of the process, the requested item (authenticated if required) , is available. The online interactions make the process very fast, improving the perceived quality and user satisfaction. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | The application of information technologies to the government process reduces the time to perform the task improving the efficiency. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | User, Public Boby, Certifier service, E-payment service | ||
| + | |||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG3. Business Goal TIS-BG-3 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-3 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Provide a 24h per day availability of the services | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | User may submit a request at any time and from anywhere, so service availability must be always guaranteed. User can access from anywhere in the world and can have a different time zone. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | The infrastructure must guarantee a 24x7 availability of the services. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | User and Public Body | ||
| + | |||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG1. Business Goal TIS-BG-4 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-4 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Offer a good user experience and provide continuous feedbacks to users | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | The application must be easy to use, and of quick understanding guaranteeing usability and accessibility. The usability of an application is relatedto the interface, the navigability, the positioning of text and objects. The application should offer an interface highly intuitive; information should be displayed in a directly usable format. The users of the application can have different expertise: some user could be less able than others to interact with the application; moreover disabled users could access the application. Moreover the sequence of the task should be linear, the terminology understandable, time to load pages should not be long and users should be able to easily print their information. E-government application must provide continuous feedback to guide the user during the operations. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | The e-government application must be easy to use and guide users during his operations. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | User, Public Body | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG1. Business Goal TIS-BG-5 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-5 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Guarantee confidentiality, integrity, authenticity, non-repudiation | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | E-government application must guarantee the confidentiality of the information the user provided when a service is requested. Such applications act as an interface for data that is kept in a distributed way. This can occur because of legal restrictions that aim to ensure data privacy. If data is changed, distributed transaction support is needed. Data encryption must be guaranteed for data transfers from the citizen to the public administration, among administrative offices and from a public administration to the citizen. The transfer of this data has to be encrypted to prevent the access of unauthorized persons. Messages can be signed to certify the sender of the message. A citizen can prove that he or she has sent a message through the digital signature. It is possible to prove that the recipient really received the message and that the sender really sent the message. The transmission of a document is logged in a way that it proves that the sender submitted the message and that the receiver received it. Both parties get a confirmation of this. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | E-government applications frequently have to access, receive, or store data that contains personally identifiable information such as healthcare records, criminal justice investigations and proceedings, residence and geographic records, ethnicity, and so on. The originators of messages from citizens to public offices have to be guaranteed. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | User, Public Body, Certifier service | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table BG1. Business Goal TIS-BG-6 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | ||TIS-BG-6 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Guarantee that provided information is not used for a scope different than the one required by the user | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Type | ||
| + | | Business Goals. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Description | ||
| + | | E-government application must guarantee the confidentiality of the information user provided when he requested a document. When a user requires a document, all his relevant personal information is needed, moreover if he have to pay a fee due to his request, he have to transmit information such as credit card number . It ’s important to guarantee that transmitted data are not used for different scope than the one required by the user. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Rationale | ||
| + | | When user perform a request of a document or a service, confidential data are transmitted; user must be guaranteed that data he communicated in the requests are not used for different scope. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Stakeholders | ||
| + | | User, Public Body and e-payment service | ||
| + | |||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Priority of accomplishment | ||
| + | | Should have. | ||
| + | |} | ||
| + | |||
| + | === Domain Assumptions === | ||
| + | |||
| + | == Domain Analysis == | ||
| + | |||
| + | === Strategic Dependency Model and Context Diagram === | ||
| + | |||
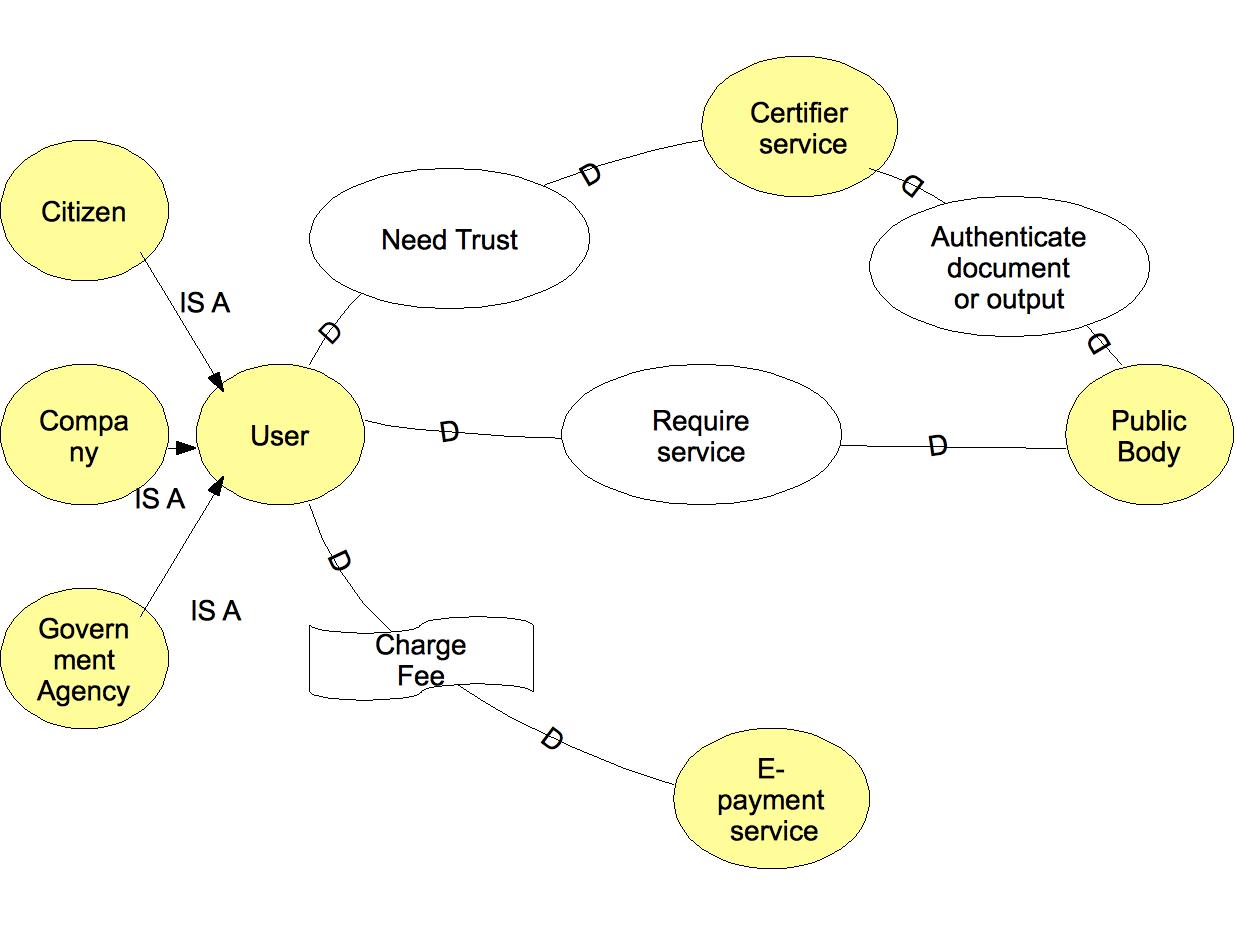
| + | In the following figure the strategic dependency diagram for the e-Government case study | ||
| + | is reported. The diagram reports the dependency between User (a Citizen, a Government Agency or a | ||
| + | Company) and Public Body to the satisfaction of the goal Require service; moreover User depends on | ||
| + | the Certifier service to gain trust on the obtained output, while the Certifier service is needed by the | ||
| + | Public Body to authenticate the service output. Moreover User needs the E-payment service to satisfy | ||
| + | the softgoal Charge Fee. | ||
| + | |||
| + | [[File:egovSDD.jpg]] | ||
| + | |||
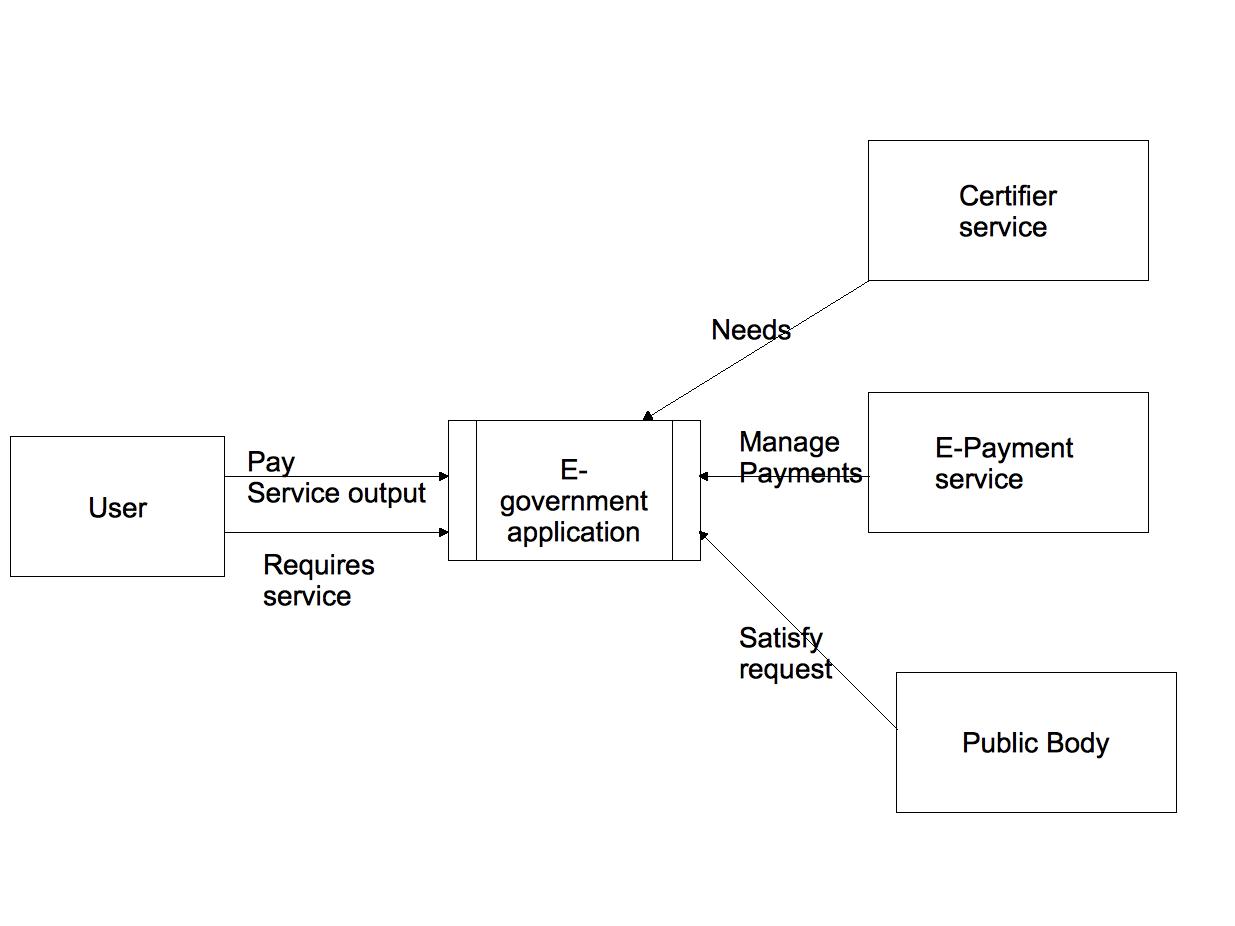
| + | The following figure represent the context diagram of the e-government case study. | ||
| + | |||
| + | [[File:egovCD.jpg]] | ||
| + | |||
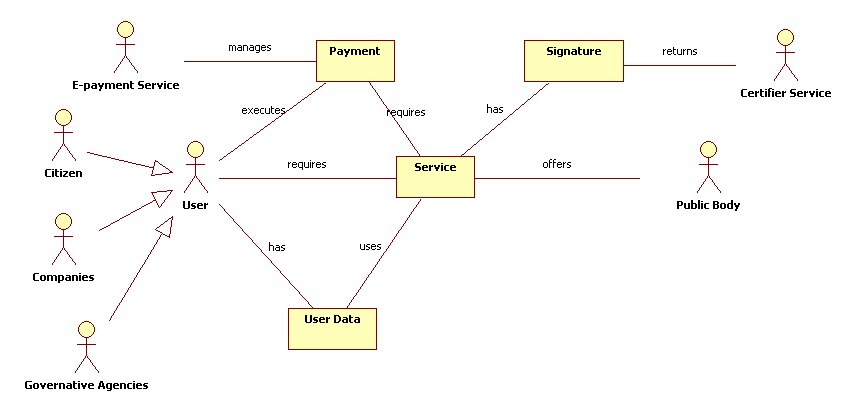
| + | In the next figure the domain model of the e-Government is reported. | ||
| + | |||
| + | [[File:egovDM.jpg]] | ||
| + | |||
| + | === Domain Model=== | ||
| + | |||
| + | == Scenarios== | ||
| + | |||
| + | In the following figure the general use case diagram for the e-Government case study is reported. | ||
| + | |||
| + | [[File:EGovUC.jpg]] | ||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table S1: Scenario TIS-ENG-1 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | | |TIS-ENG-1 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Request for e-Government service | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Related To | ||
| + | | TIS-BG-1, TIS-BG-3, TIS-BG-4, TIS-BG-5, TIS-BG-6 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Actors | ||
| + | | User | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Detailed Operational Description | ||
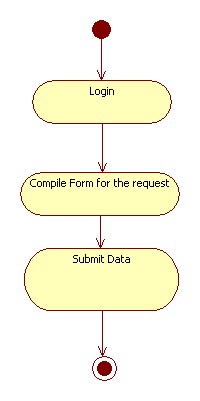
| + | | This scenario describes the submission of applications to obtain subsidies from the province of Bolzano, Italy. In the e-government application the process is started by the user that, after the login, chooses the service he needs. So the user inserts the needed data to compile the form for the request (he could decide to compile the form from the scratch or updating preexistent data). Actors involved in the scenario are the users of the application (citizen, companies or government agencies). | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Problems and Challenges | ||
| + | | When a user requires a document or a service he submits a lot of personal data. The confidentiality of the data must be guaranteed by the application, moreover the user must be assured that provided data are not used outside that transaction. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Additional Material | ||
| + | | [[File:EGovAD1.jpg]] | ||
| + | |||
| + | |||
| + | |} | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table S2: Scenario TIS-ENG-2 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | | |TIS-ENG-2 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Pay requested service | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Related To | ||
| + | | TIS-BG-5, TIS-BG-6 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Actors | ||
| + | | User, E-payment servi | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Detailed Operational Description | ||
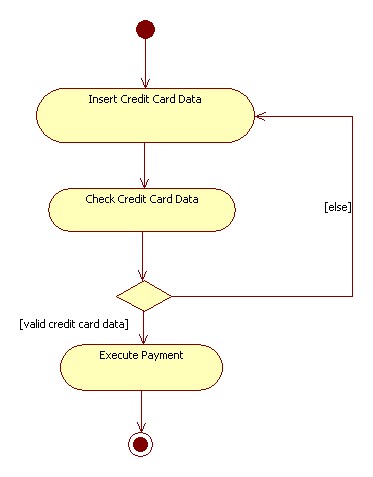
| + | | If the user needs to pay some fee to obtain the requested service, he must interact with the e-payment service. The user inserts the needed data (usually credit card number) and waits for the completion of the process. The e-payment service checks the inserted data for the payment. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Problems and Challenges | ||
| + | | A mechanism of encryption of data must be guaranteed to protect the transmission of confidential data by intrusion. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Additional Material | ||
| + | | [[File:EGovAD2.jpg]] | ||
| + | |||
| + | |||
| + | |} | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table S3: Scenario TIS-ENG-3 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | | |TIS-ENG-3 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Output Authentication | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Related To | ||
| + | | TIS-BG-5, TIS-BG-6 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Actors | ||
| + | | User, E-Certifier service | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Detailed Operational Description | ||
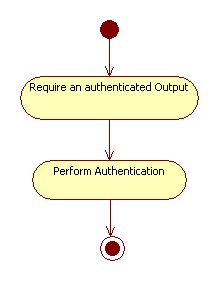
| + | | The user could require an authenticated output, so the application has to provide a mechanism to certify the output. | ||
| + | |||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Problems and Challenges | ||
| + | | A mechanism of digital signature must be provided to guarantee the authentication of the output. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Additional Material | ||
| + | | [[File:EGovAD3.jpg]] | ||
| + | |||
| + | |||
| + | |} | ||
| + | |||
| + | |||
| + | {| style="background:#cccc99;color:black;width:80%;" border="1" cellpadding="5" cellspacing="0" align="center" | ||
| + | |+ Table S4: Scenario TIS-ENG-4 | ||
| + | !Field !! Description | ||
| + | |||
| + | |- style="background:#f0f0f0; color:black" | ||
| + | ! UniqueID | ||
| + | | |TIS-ENG-4 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Short Name | ||
| + | | Satisfy Request | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Related To | ||
| + | | TIS-BG-2 | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Involved Actors | ||
| + | | User, Public Body | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Detailed Operational Description | ||
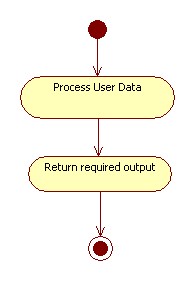
| + | | Data submitted by the user when an eGovernment service is requested, are used by the Public Body to satisfy the user requests. At the end of the process the User receives the required output. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Problems and Challenges | ||
| + | | A mechanism of digital signature must be provided to guarantee the authentication of the output. | ||
| + | |||
| + | |- style="background:white; color:black" | ||
| + | ! Additional Material | ||
| + | | [[File:EGovAD4.jpg]] | ||
| + | |||
| + | |||
| + | |} | ||
Latest revision as of 09:38, 19 May 2011
Contents
Description
Usually when a citizen needs some document from the public sector, he has to go to the appropriate department; often the time spent in queues, and the time spent to reach the right office is very long. E-Government is the process to make information technologies available to the government services in order to improve the relationships between citizens and their governments (public sector could be made open and transparent to the citizens). One of the services made available to the user, is the possibility to submit applications to require some service, and receive replies online. At any time during the day, from their locations citizens can access to the offered services and obtain all the needed information without spending any time in queues. In such a way, e-government is able to improve the efficiency of public sector, avoiding the time spent to reach different offices or waiting in queue, resulting in an improvement of the offered services and a better accessibility and transparency of the public services. Not only citizens may be the the users of the government application, but we can image that all the government agencies of a city could share data about the citizens and have the need to access to the services of the application, in order to make available, at any time, all the needed information. The case study is derived from the EU project NEXOF. In particular, it has been proposed by Engineering Ingegneria Informatica and TIS. We have mapped it into the format proposed for S-Cube, retrieving the business goals and the scenarios needed for our description.
Business Goals and Domain Assumptions
In the following sections will be reported the Business Goals and the Domain Assumptions for the current case study.
Business Goals
| Field | Description |
|---|---|
| UniqueID | TIS-BG-1 |
| Short Name | Statewide provision of online services for citizens, companies, government agencies |
| Type | Business Goals. |
| Description | The infrastructure must be able to make services of the public sector available to all the users, such as citizens, companies or government agencies. Each user can access, from somewhere, to the services providing login information; after the login the user can have the possibility to forward requests of some documents or require any service. |
| Rationale | Essentially the rationale is the capability to make available the services offered by the public sector to citizens, companies and government agencies. |
| Involved Stakeholders | Users and Public Body
|
| Priority of accomplishment | Should have. |
| Field | Description |
|---|---|
| UniqueID | TIS-BG-2 |
| Short Name | Improve speed and efficacy of processes |
| Type | Business Goals. |
| Description | The infrastructure must be able to serve quickly the user requests. When a citizen requires a service, replies are received online. Moreover if a fee must be paid, user could access, easily, the e-payment service. At the end of the process, the requested item (authenticated if required) , is available. The online interactions make the process very fast, improving the perceived quality and user satisfaction. |
| Rationale | The application of information technologies to the government process reduces the time to perform the task improving the efficiency. |
| Involved Stakeholders | User, Public Boby, Certifier service, E-payment service
|
| Priority of accomplishment | Should have. |
| Field | Description |
|---|---|
| UniqueID | TIS-BG-3 |
| Short Name | Provide a 24h per day availability of the services |
| Type | Business Goals. |
| Description | User may submit a request at any time and from anywhere, so service availability must be always guaranteed. User can access from anywhere in the world and can have a different time zone. |
| Rationale | The infrastructure must guarantee a 24x7 availability of the services. |
| Involved Stakeholders | User and Public Body
|
| Priority of accomplishment | Should have. |
| Field | Description |
|---|---|
| UniqueID | TIS-BG-4 |
| Short Name | Offer a good user experience and provide continuous feedbacks to users |
| Type | Business Goals. |
| Description | The application must be easy to use, and of quick understanding guaranteeing usability and accessibility. The usability of an application is relatedto the interface, the navigability, the positioning of text and objects. The application should offer an interface highly intuitive; information should be displayed in a directly usable format. The users of the application can have different expertise: some user could be less able than others to interact with the application; moreover disabled users could access the application. Moreover the sequence of the task should be linear, the terminology understandable, time to load pages should not be long and users should be able to easily print their information. E-government application must provide continuous feedback to guide the user during the operations. |
| Rationale | The e-government application must be easy to use and guide users during his operations. |
| Involved Stakeholders | User, Public Body |
| Priority of accomplishment | Should have. |
| Field | Description |
|---|---|
| UniqueID | TIS-BG-5 |
| Short Name | Guarantee confidentiality, integrity, authenticity, non-repudiation |
| Type | Business Goals. |
| Description | E-government application must guarantee the confidentiality of the information the user provided when a service is requested. Such applications act as an interface for data that is kept in a distributed way. This can occur because of legal restrictions that aim to ensure data privacy. If data is changed, distributed transaction support is needed. Data encryption must be guaranteed for data transfers from the citizen to the public administration, among administrative offices and from a public administration to the citizen. The transfer of this data has to be encrypted to prevent the access of unauthorized persons. Messages can be signed to certify the sender of the message. A citizen can prove that he or she has sent a message through the digital signature. It is possible to prove that the recipient really received the message and that the sender really sent the message. The transmission of a document is logged in a way that it proves that the sender submitted the message and that the receiver received it. Both parties get a confirmation of this. |
| Rationale | E-government applications frequently have to access, receive, or store data that contains personally identifiable information such as healthcare records, criminal justice investigations and proceedings, residence and geographic records, ethnicity, and so on. The originators of messages from citizens to public offices have to be guaranteed. |
| Involved Stakeholders | User, Public Body, Certifier service |
| Priority of accomplishment | Should have. |
| Field | Description |
|---|---|
| UniqueID | TIS-BG-6 |
| Short Name | Guarantee that provided information is not used for a scope different than the one required by the user |
| Type | Business Goals. |
| Description | E-government application must guarantee the confidentiality of the information user provided when he requested a document. When a user requires a document, all his relevant personal information is needed, moreover if he have to pay a fee due to his request, he have to transmit information such as credit card number . It ’s important to guarantee that transmitted data are not used for different scope than the one required by the user. |
| Rationale | When user perform a request of a document or a service, confidential data are transmitted; user must be guaranteed that data he communicated in the requests are not used for different scope. |
| Involved Stakeholders | User, Public Body and e-payment service
|
| Priority of accomplishment | Should have. |
Domain Assumptions
Domain Analysis
Strategic Dependency Model and Context Diagram
In the following figure the strategic dependency diagram for the e-Government case study is reported. The diagram reports the dependency between User (a Citizen, a Government Agency or a Company) and Public Body to the satisfaction of the goal Require service; moreover User depends on the Certifier service to gain trust on the obtained output, while the Certifier service is needed by the Public Body to authenticate the service output. Moreover User needs the E-payment service to satisfy the softgoal Charge Fee.
The following figure represent the context diagram of the e-government case study.
In the next figure the domain model of the e-Government is reported.
Domain Model
Scenarios
In the following figure the general use case diagram for the e-Government case study is reported.